2020网鼎杯RE WP
re_bang
jeb拖进去一看,梆梆加固免费版,掏出Frida直接dump,具体可看之前写的这篇 使用Frida给apk脱壳并穿透加固Hook函数 。
dump出三个dex,看下大小基本确定了解密后的dex
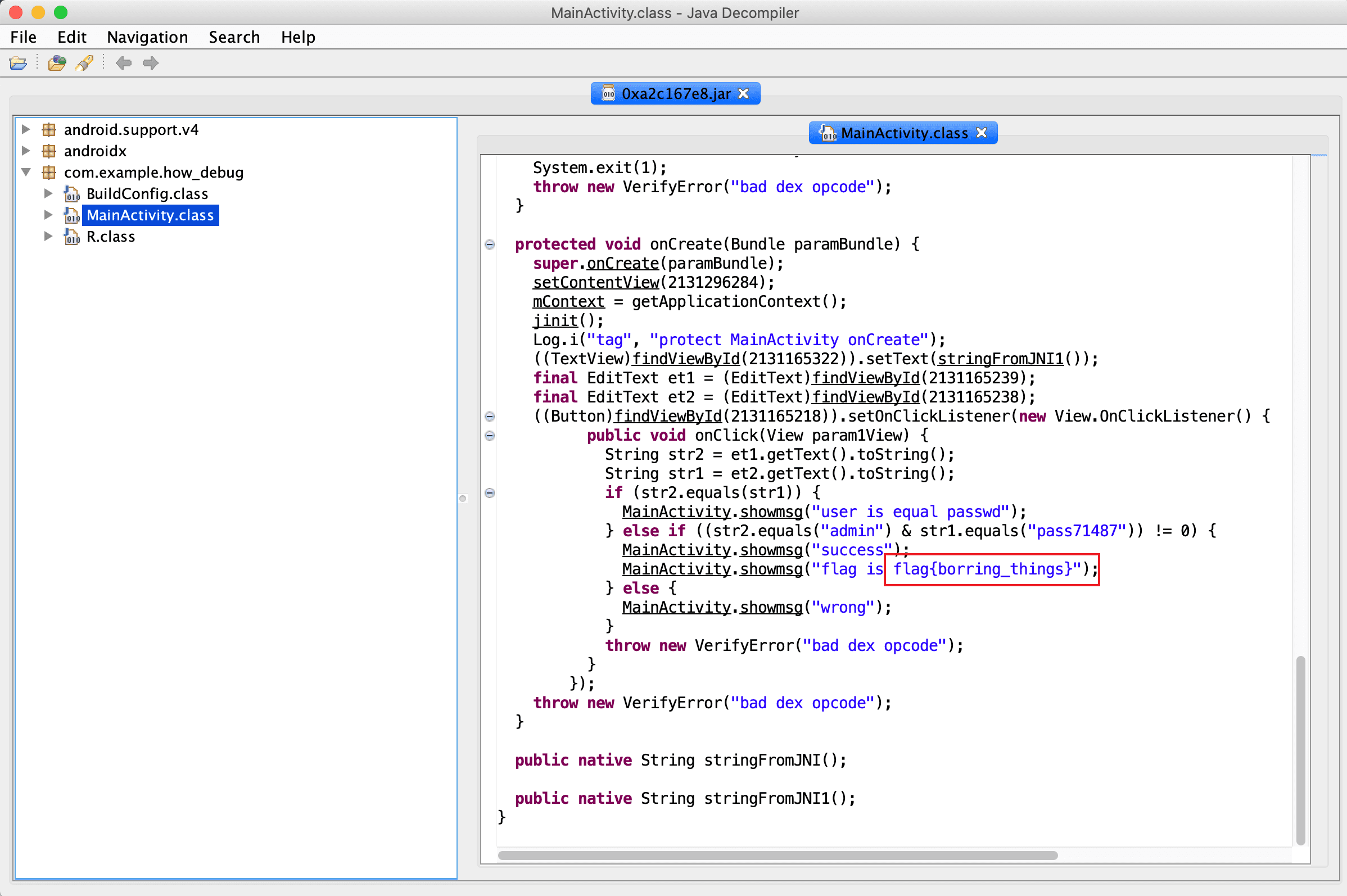
由于分析dex不太舒服,就直接转jar拿jd-gui看了,没想到flag直接硬编码。
signal
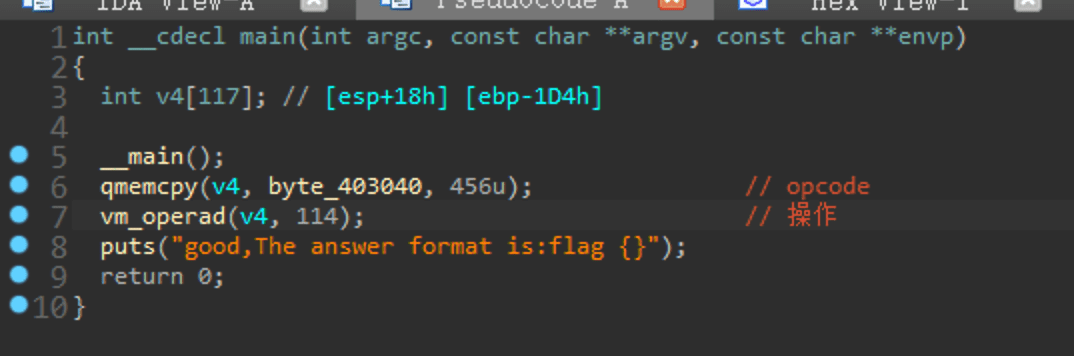
简易VM,没什么可说的,进去就能看到逻辑
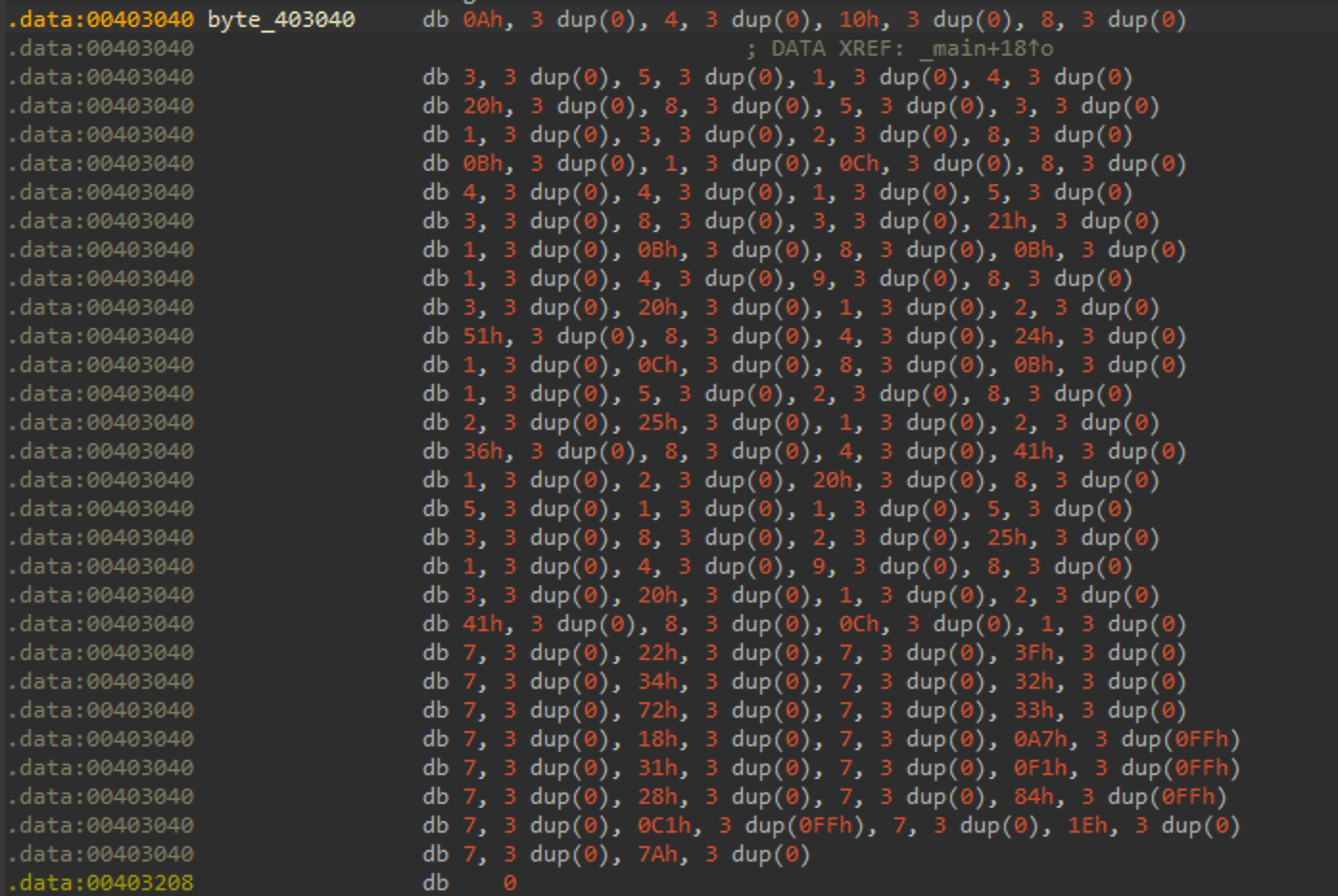
先把opcode提取出来,456个字节,把0去了,还剩114字节(456/4)
Code
10,4,16,8,3,5,1,4,32,8,5,3,1,3,2,8,11,1,12,8,4,4,1,5,3,8,3,33,1,11,8,11,1,4,9,8,3,32,1,2,81,8,4,36,1,12,8,11,1,5,2,8,2,37,1,2,54,8,4,65,1,2,32,8,5,1,1,5,3,8,2,37,1,4,9,8,3,32,1,2,65,8,12,1,7,34,7,63,7,52,7,50,7,114,7,51,7,24,7,167,255,255,255,7,49,7,241,255,255,255,7,40,7,132,255,255,255,7,193,255,255,255,7,30,7,122 |
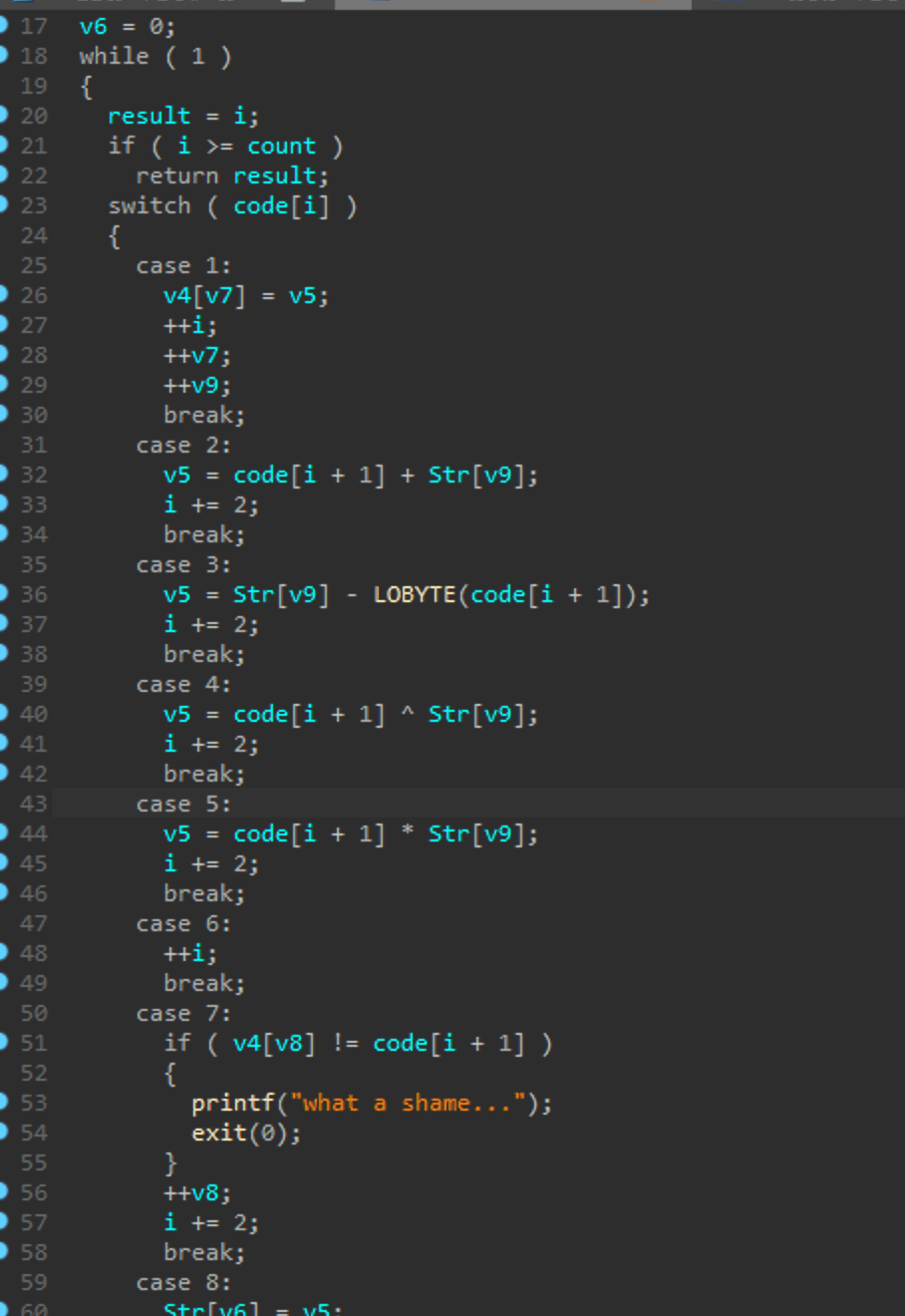
然后看vm操作,就12个case
解法1
直接写脚本提取一下看看(骚操作之print指令)
python
code=[ |
得到
python
read(Str) |
还是挺有规律的,一组就是一个handle,借个看雪的分析吧,自己的太乱
Code
10h ^ input[1]-5 = 22h |
这么头铁的解法当然是不够优雅的,且看下面符号执行
解法2
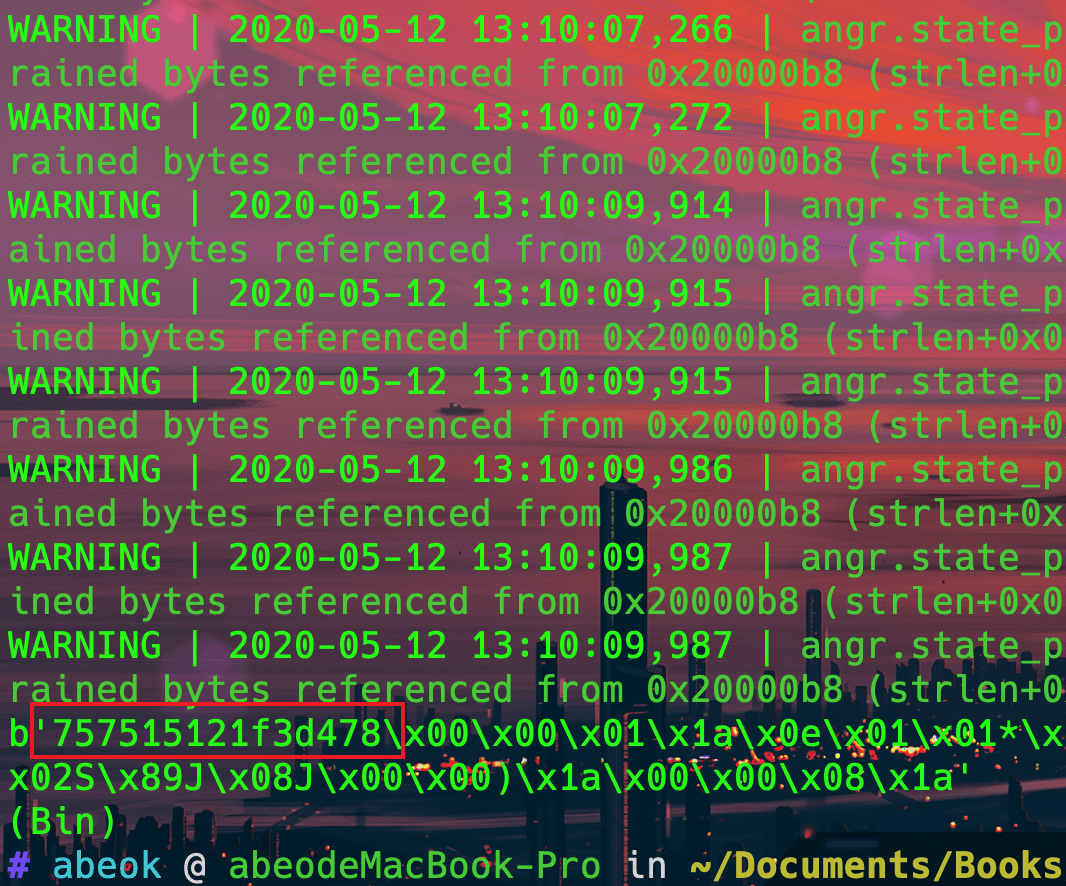
angr直接跑
python
import angr |
几秒钟完事,十分枯燥
jocker
这道题怎么说,男默女泪,最后四个字节还得靠猜???
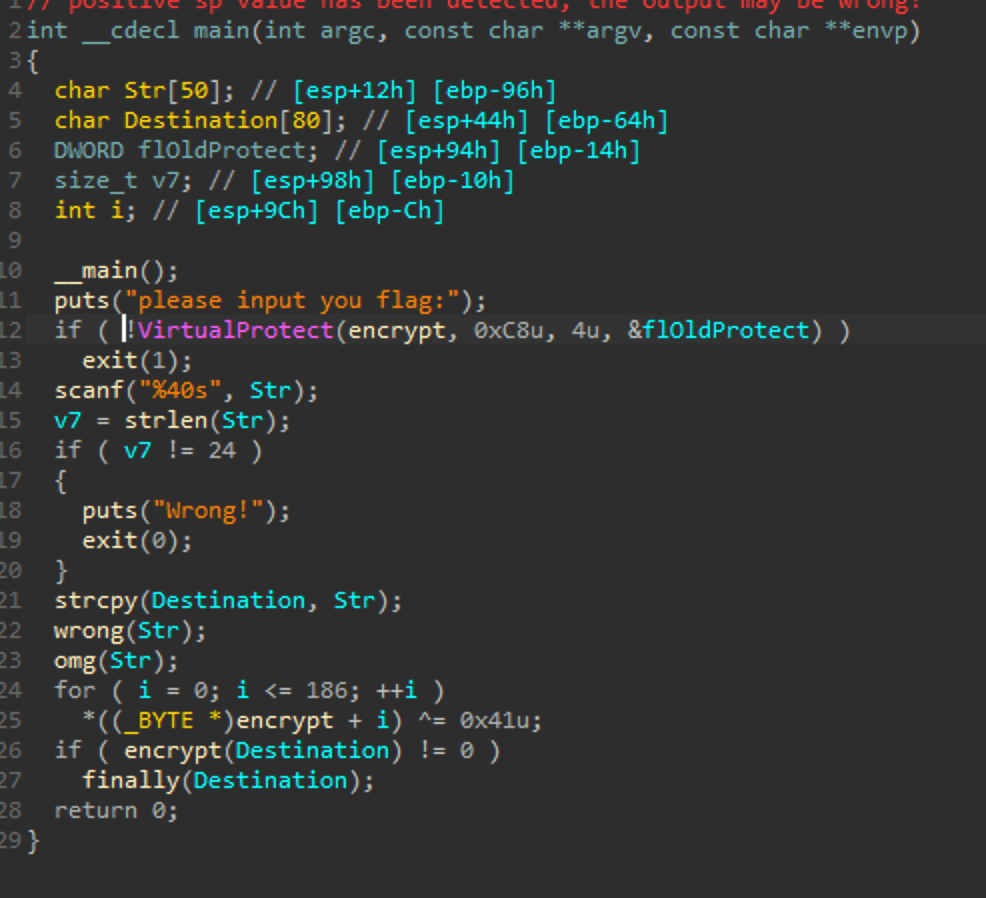
ida看一下,是简单的SMC
直接od调到解密后dump出来,要解密的地址是401500
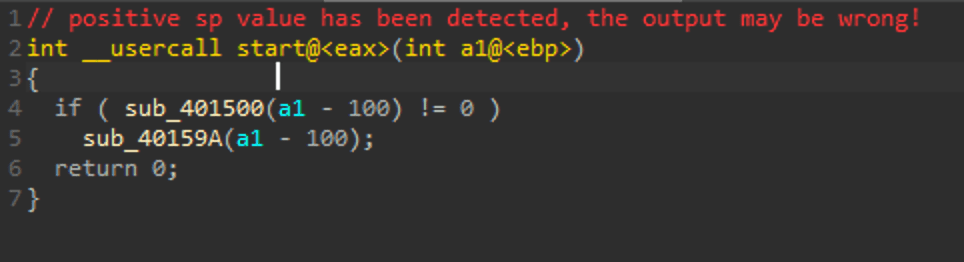
dump以后再用ida看看,一共解密出两个函数
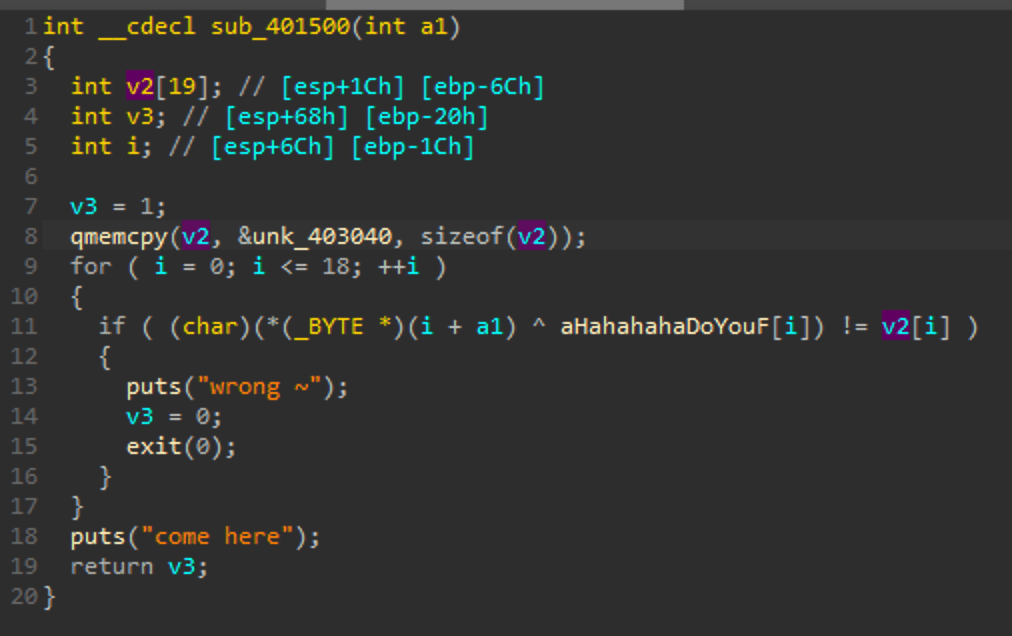
查看401500
写脚本逆一下
python
key2 = [0x0E, 0x0D, 0x09, 0x06, 0x13, 0x05, 0x58, 0x56, 0x3E, 0x06, 0x0C, 0x3C, 0x1F, 0x57, 0x14, 0x6B, 0x57, 0x59, 0x0D] |
得到一部分flag
Code
flag{d07abccf8a410c |
未解密前有个假flag
python
key1=[0x66, 0x6B, 0x63, 0x64, 0x7F, 0x61, 0x67, 0x64, 0x3B, 0x56, 0x6B, 0x61, 0x7B, 0x26, 0x3B, 0x50, 0x63, 0x5F, 0x4D, 0x5A, 0x71, 0x0C, 0x37, 0x66] |
比较发现还少5个字符,当然了,最后一个肯定是}
再看看另一个函数
看到剩下五个字符,不过被加密了
这就纯靠猜了
最后v7肯定是}加密过来的,试试这两个异或,得到71,其他四个字符都异或71,最后得到b37a}拼起来就行。
或者。。。直接爆破
python
import subprocess |